- 39 Posts
- 28 Comments

 1·1 year ago
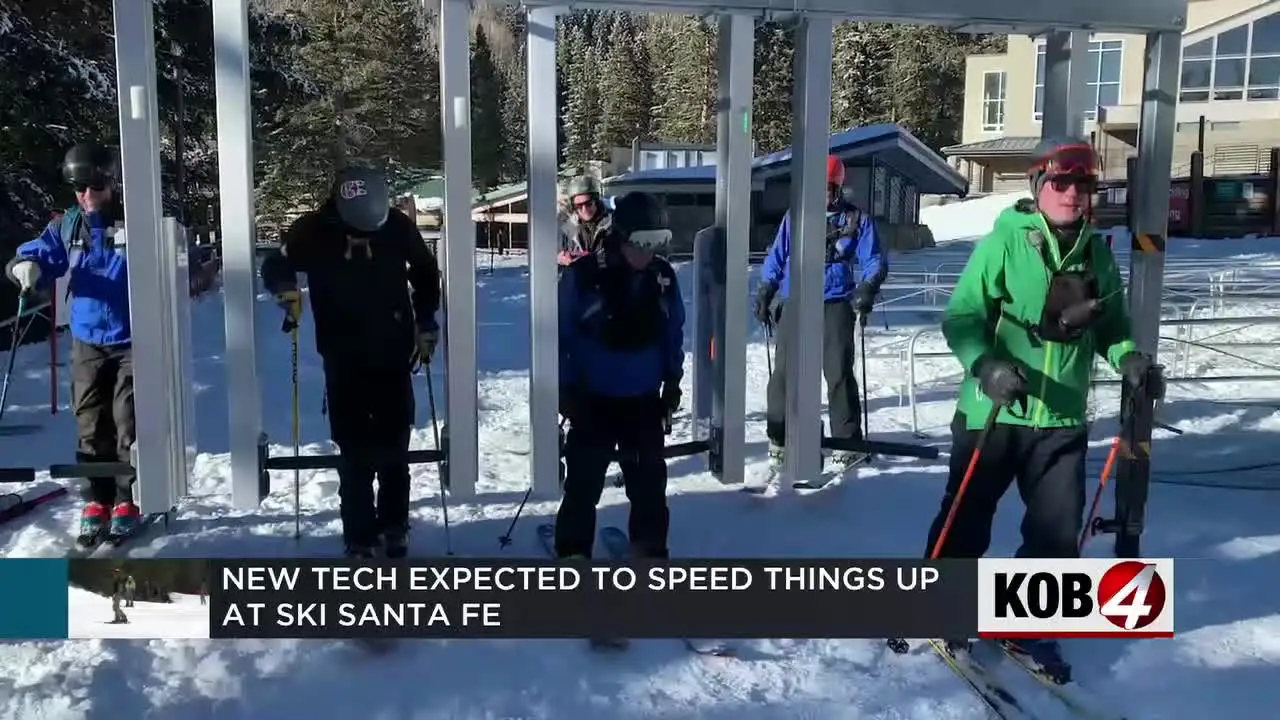
1·1 year agoI know this isn’t technically ABQ, but I drive up to Ski Santa Fe multiple times each winter and I’m guessing other people in this community do as well. The new technology mentioned in this article made it interesting to me.
The RFID passes aren’t a big deal, but they are kind of nice. They could be finicky when trying to get on the lift when I had them at Red River, no better or worse than having someone manually scan passes. But being able to reload them without visiting the ticket office in the morning was great.
But this is the first time I’ve heard about the high-speed detachable lifts coming to Santa Fe, and I’m really looking forward to that even though it won’t be there until next winter. I’ve only gotten to try them once, in Winter Park, CO, and spending half as much time sitting on a lift makes the day so much better.

 1·1 year ago
1·1 year agoThe stadium still needs to get approved by City Council, but this was another step on the way that has been passed.

 3·1 year ago
3·1 year agoI don’t know if anyone here actually cares enough to go an provide input, but it’s nice to be aware that construction here is coming up a few years down the line.
The website for the project also mentions that reconstructing the I-25/Gibson interchange is further down the line. And also, construction on the Montgomery and Comanche interchanges with I-25 should be starting next year.

 71·1 year ago
71·1 year agoAre you calling for a ban on human driven cars? They killed more than zero people yesterday! If you aren’t, you’ve accepted a human-driven vehicular homicide rate above zero.

 6·1 year ago
6·1 year agoI’ve always been pretty underwhelmed by In-N-Out, which has been fine the times I’ve tried it but never seems to live up to the hype. But having more options is nice (or will be, in 2027), although I’ll make sure to wait at least a few weeks for the initial hype to die down.
Now, let me know when Culver’s will be showing up…

 262·1 year ago
262·1 year agoI mean, that sucks, but it’s not like things are going to get better once you’re outside of the conditions mentioned

 2·1 year ago
2·1 year agoKind of mixed on this. I think new EV infrastructure is good, and I think apartment complex (especially need ones) should be providing ways for residents to charge EVs. But requiring every new business to build EV charging in their parking lot seems like expensive overkill.

 3·1 year ago
3·1 year agoOK, so I looked though my browser history, and here are some relevant pages I found:
- keepassxc-browser Issue 1267
- keepassxc-browser Issue 1631
- keepassxc-browser Issue 1783
- browserpass-native Issue 93
I don’t remember how much I used each one, but eventually I pieced together enough information information to get the Browserpass extension working in the Google Chrome flatpak. But three of those links are KeePassXC, which should be useful for adapting this for your use.
The main file that was having problems was the Browserpass Native Messaging Hosts file in my config directory for the Chrome flatpak,
~/.var/app/com.google.Chrome/config/google-chrome/NativeMessagingHosts/com.github.browserpass.native.json. Originally it was a symlink to a file at/usr/lib/browserpass/hosts/chromium/com.github.browserpass.native.json:{ "name": "com.github.browserpass.native", "description": "Browserpass native component for the Chromium extension", "path": "/usr/bin/browserpass-linux64", "type": "stdio", "allowed_origins": [ "chrome-extension://naepdomgkenhinolocfifgehidddafch/" ] }The call to
/usr/bin/browserpass-linux64did not see to work for me, so I ended up making a copy of the file in theNativeMessagingHostsdirectory and modified it to point to a script in my home mount:wile_e8 NativeMessagingHosts $ diff com.github.browserpass.native.json.orig com.github.browserpass.native.json 4c4 < "path": "/usr/bin/browserpass-linux64", --- > "path": "/home/wile_e8/.config/browserpass/browserpass.sh",I don’t remember why I picked to do it inside the
~/.configdirectory, but it worked so I left it. And here is the script I put at~/.config/browerpass/browserpass.sh:#!/bin/sh cd ~ /usr/bin/flatpak-spawn --host /usr/bin/browserpass-linux64 2>/tmp/error.logI don’t remember how I came up with that script, it must be somewhere in the four links at the top.
Finally, I needed to use Flatseal to allow access to the script. In the Google Chrome settings, under “Filesystem->Other files”, I added an entry saying
~/.config/browserpass:ro. Also modified from the default in Flatseal, I have “Filesystem->All user files” enabled, along with “Socket->D-Bus session bus” and “Socket->D-Bus system bus”. I don’t know how necessary the last three are, but I’m not messing with it now that I have it working.So, that’s what I did to get the Browserpass extension working in the Google Chrome flatpak. You’ll have to modify some things to get it working for KeePassXC, or for Firefox. But that general pattern should work.

 3·1 year ago
3·1 year agoKeep an eye out, I’ll come back to this. It involves posting config file diffs and a script I wrote, it’ll be a longer post I don’t have the time to write right at this moment.
But yes, the fact that I need to find the time to post all the changes I needed to make to get this to work is part of the problem here.

 3·1 year ago
3·1 year agoFWIW I figured out how to get a password manager (Browserpass, not KeePassXC) to communicate with flatpak Chrome if you want some advice on how to get it to work.
But yes, it was way more difficult than it should have been (which is “should work out of the box, just like a regular package”). So if you’re just listing some of the shortcomings of flatpak, never mind.

 91·1 year ago
91·1 year agoIt’s kind of amazing it took this long - I don’t know why they didn’t do it this way from the start.

 11·1 year ago
11·1 year agoWait, are photo passes really happening this time? Google has made a couple of blog posts announcing the feature, but I’ve been regularly checking for the last several months and haven’t seen it. It was a nice feature of the original Google Wallet that was removed in one of the rebrands, I’d really like it to actually be back instead of just “coming soon” (not that soon)

 3·1 year ago
3·1 year agoYikes. I haven’t been to Los Pookies yet, but it was on my list of restaurants I thought I should try soon. But reading that inspection, maybe it’s a good thing I haven’t gone there.

 2·1 year ago
2·1 year agoThe and Journal has one in the images at the top of the page - https://www.abqjournal.com/news/now-its-real-lease-agreement-puts-united-soccer-stadium-at-balloon-fiesta-park-a-step/article_483d36e2-5f17-11ee-8af8-6bf74e6e6b79.html
Is there any mirror for this? I don’t know if this has been posted to some other site as well, but the web site seems to be overloaded with traffic right now and I can’t see the article.

 4·1 year ago
4·1 year agoI stopped posting this regularly because they were mostly boring and nobody else seemed interested. But this is the second week in a row where the Smith’s at Wyoming and Paseo del Norte is in the red, which seems bad.

 1·1 year ago
1·1 year agoIf nothing else, Slice and Dice Pizzeria sounds like it should be worth a try. Has anyone been to the McMahon location? Is it any good?

 3·1 year ago
3·1 year agoThe United States. And I’ve been checking for it since it was originally announced at the beginning of June. And… I guess another announcement means it’s not dead. Yet.

 5·1 year ago
5·1 year agoWhen will Google Wallet Pass photo import actually go live? It was announced over three months ago, and I’ve been checking for it ever since. Will this announcement mean it’s actually going to show up in the next day or three, or will I be checking in vain for several more months?











I don’t know how many people take the Tram in the middle of the winter, especially since the ski area hasn’t opened the past few years. But it won’t be open if you try. Hopefully the promised “quicker trips during busy periods” will materialize.