FYI!!! In case you start getting re-directed to porn sites.
Maybe the admin got hacked?
edit: lemmy.blahaj.zone has also been hacked. beehaw.org is also down, possibly intentionally by their admins until the issue is fixed.
Post discussing the point of vulnerability: https://lemmy.ml/post/1896249
Yea, I switched to this alt. It appears to be one of the assistant admins accts. Seems like an old fashioned anon prank, to me, they’re mainly just trying to make stuff offensive and redirect people to lemonparty.
So, y’know, old school.
I don’t know if any data is actually in danger, but I doubt it. I don’t see why assistant admins would need access to it.
All the bean memes are in danger! On a serious note, old-skool or not, it’s a huge loss of trust in something the community-at-large is excited to see replace reddit.
Par for the course. This system will never be immune to things like that. That’s part of what happens when you decentralize your power. Instead of a single target that can be made highly secure, you have a distributed array of targets.
People should certainly be engaging on here with full awareness of the reality of the Fediverse, not expecting reddit 2.0. We never will be able to offer exactly what they did. We’ll be naturally worse in some areas and naturally better in others.
This is why I’m glad I made redundant accounts on multiple instances. When there are problems on lemmy.world, I can just hop on over to another. That’s never been an option with Reddit.
Now if there was only a way to export or sync user settings like subscriptions, it would be perfect.
There’s actually another thread on exactly this topic: https://lemmy.ml/post/1875767
Is there a way to link posts in the context of the reader’s instance? Like with !c community links?
I don’t think so, but I’d love to be proven wrong!
That’s fair. I shouldn’t have said “replace reddit.”
On the other hand, look at where we are. This is proof that one hack can’t take down Lemmy.
True that. If you look at posts on lemmy.world though, it’s clear their users (which is like 50% of Lemmy) have zero clue they’re defederated ATM, and probably many that don’t know it’s compromised.
Federation and decentralization are not Web 2.0 concepts. Just like people who first learned what a tweet and a follow were and all the other concepts of those social media platforms, they’ll learn the new paradigm. Or they won’t and we’ll stick to 2.0 platforms.
i did switch from reddit to lemmy.world because i expected it to be a safe alternative that would atleast pay a lot of attention to security. so yes, the trust in security is broken a lot with this. especially since it happend so soon after so many people joined. i already think about maybe making my own instance to keep my account safe in the future.
My concern is that configuring the site to automatically redirect users sounds like they have pretty large control over the site - the kind of control that I would assume is usually limited to users with root access on the server.
Obviously hope nothing of value is lost and that there is a proper off-site backup of the content.
Edit: See Max-P’s comment, it looks like the site redirection was accomplished in a way that IMO suggests they do NOT have full control over the site. We’ll obviously have to wait for the full debrief from the admins.
If it was just DNS that doesn’t mean too much. If it was just DNS it seems to be back up. It’s like changing the number in a phone book.
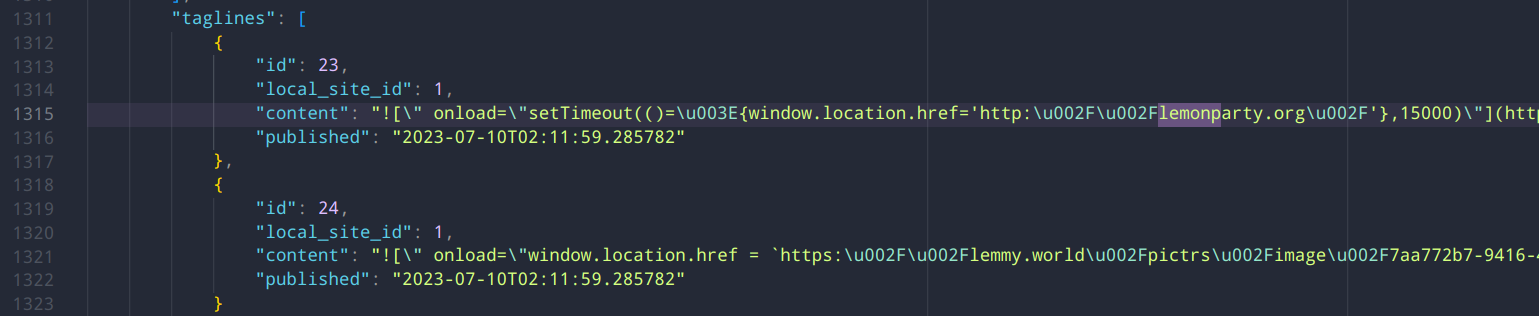
It was a JavaScript injection to the site’s sidebar and top announcement section
Yeah the “redirect somewhere else” attack definitely doesn’t necessarily require any particular control of the site. Usually it’s noticing that you can trick some text into being run as Javascript, instead of interpreted as text… And then you just stick in a cheeky little
<notarealscript>window.location = "https://www.badsite.horse"</notarealscript>into that spot.Then every time that comment, username, (in this case apparently) custom emoji, etc. gets loaded, whoops, the code runs and off you go!
So no control of the site is required at all.
I don’t see why assistant admins would need access to it.
because it’s easier than figuring out what permissions they actually need
Main instance hacked? Time to use an alt!
The first hack is a rite of passage for every site that gets big. It means we’ve been recognized!
Luckily, this seems to be a standard troll (with some tech knowledge) - they’ve defaced the site and put redirects to shock sites, rather than injecting actual malware or quietly collecting everyone’s passwords. This could be much worse.
I tried to reproduce the exploit on my own instance and it appears that the official Docker for 0.18.1 is not vulnerable to it.
It appears that the malicious code was injected as an
onloadproperty in the markdown for taglines. I tried to reproduce in taglines, instance info, in a post with no luck: it always gets escaped properly in the<img alt="exploit here">property as HTML entity.lemmy.world appears to be running a git commit that is not public.
I actually consider it good news that the redirection is happening this way (something that can be done just by having the lemmy credentials of an admin) vs something indicating they have access to the server itself.
Yep, same. It was also the most likely scenario.
It looks like it was an individual admin getting hacked. Not good but not the worst. Most fallout will probably be whether their security practices were sufficient for an admin and whether lemmy has good enough contingencies for this sort of thing. Lemmy’s 2FA is probably a hot issue now though.
OK good to know that the server itself is unlikely to be compromised. I’ll be changing passwords to all my accounts once this blows over.
It does look like most instances will be vulnerable judging by the fix. It’s not custom code; it’s in lemmy-ui proper.
It seems the database and the server itself is not compromised? Just an admin account that used to post a markdown XSS exploit?
Pretty much, and it’s not even XSS (it’s not cross-site), it’s just plain basic HTML injection breaking out of Markdown. At least as far as I was able to find.
XSS is a blanket term for vulnerabilities that allows attackers to inject client-side scripts. Looks like someone is already identified and submitted a pull request that contain a fix: https://github.com/LemmyNet/lemmy-ui/pull/1897/files
Aaaargh yeah using typescript doesn’t do jack when your API is stringly-typed. This erm wouldn’t have happened on the backend.
Last I saw, they were on 0.18.1, unless a very recent update was installed. Do you happen to have a full list of domains they were redirecting to? Just want to be sure they were only going to “harmless” offensive sites, and not something worse.
Only lemonparty (which then redirects to chaturbate) and the pedo image hosted in the pictrs of lemmy.world itself. I saw no evidence of anything else, as people said, it’s a pretty oldschool type of hack to disturb not spread malware.
But I didn’t dig that much further than that, and it’s only a snapshot of what I gathered before it got fixed. I Ctrl+F “lemonparty” in view source and pasted the JSON in VScode and that’s about it. Didn’t dig much deeper if that was just a red herring.
Thanks for digging in and sharing your findings!
As for the version, my instance reports it as
0.18.1-2-ga6cc12afeSo it seems to be using some extra patches, but I can’t find that commit on GitHub which indicates it might not be public, or cherry-picked locally.
So with this in mind, either it’s just innocent performance patches, or someone potentially also introduced the markdown vulnerability.
Although it’s also entirely possible I suck and wasn’t able to reproduce it correctly/had wrong quoting or something. Hopefully the devs can shine some light in the details.
Max-P doing the Lord’s work
How did it happen and what does this mean for me as a user of lemmy.ml who also follows people on lemmy.world?
One of the admin accounts appears to have been compromised. The owner/other admins appear to be aware now because that account had its admin access revoked and offending posts are being removed.
Definitely opens up a big question about the security of Lemmy instances that I am sure will be discussed over the next few days.
I wouldn’t assume reasons why or that it’s fixed until that consensus has been more widely reached.
More time will definitely be needed. I’m glad they caught it and acted quickly enough to prevent more vandalism from occurring, but until we know how the account was compromised and what else they may have gotten in the process, it’s still a situation to keep an eye on.
They are still acting on it, seems.
Yep, it’s definitely not over.
Definitely opens up a big question about the security of Lemmy instances that I am sure will be discussed over the next few days.
They added 2FA login to lemmy in one of the newer updates. Probably pretty pertinent for any admins to use it…
It’s buggy and missing some key checks to make sure it’s working when you set it up.
Real risk of locking yourself out of your account.
oh, really? maybe i’ll turn mine off then…Thanks for the heads up!
Mostly a risk on initial setup.
I’ve been waiting a bit for it to stabilize and just using huge random passwords
If you’re using a password manager you’d be doing this for every site and without even having to think about it. Bitwarden is a great choice.
I like KeePass. Bitwarden currently has an nginx exposure in the Dockerfile published in their git repo (may have been fixed since a couple of days ago). That said, I used Bitwarden for many years and switched out of an abundance of paranoia, and am definitively not recommending against it. Just basically use one of the following:
- Bitwarden
- KeePass
- 1password
And stay far the fuck away from LastPass
Oh I do. Used Bitwarden for many years.
I actually use keepass for totp codes too.
Also I believe this was achieved through cookie stealing, which 2FA would not have helped
Too bad it doesn’t work with several 2FA apps and right now…
Thanks for the context
They really need to improve their 2fa implementation
Not a whole lot - you might see some spam being federated from lemmy.world but I’d expect the lemmy.ml and lemmy.world admins will fix it, and them clean it up.
That’s probably good stress test to figure out how to handle that.
Thanks for the response very helpful.
Removed by mod
GitHub PR fixing the bug: https://github.com/LemmyNet/lemmy-ui/pull/1897/files
If your instance has custom emojis defined, this is exploitable everywhere Markdown is available. It is NOT restricted to admins, but can be used to steal an admin’s JWT, which then lets the attacker get into that admin’s account which can then spread the exploit further by putting it somewhere where it’s rendered on every single page and then deface the site.
If your instance doesn’t have any custom emojis, you are safe, the exploit requires custom emojis to trigger the bad code branch.
I see a new lemmy-ui docker image has been pushed an hour ago, tagged
0.18.2-rc.1. Anyone know if it fixed the issue?Edit: yep, it’s fixed: https://github.com/LemmyNet/lemmy-ui/commit/e80bcf53acb8ce25ed5ef6b7eb16b90f0b07e8f1
But won’t custom emojis from remote instances still trigger the exploit?
Apparently the custom emojis are rendered as static images when federated to outside instances so it’s clean.
I’m not particularly familiar with XSS but I’m curious how a frontend exploit can compromise an instance?
Presumably the injected XSS stores the admin’s JWT somewhere for the exploiter?
Then using that JWT they can effectively login as the admin which gives them access to whatever admin dashboard there is, but does that actually compromise the backend at all?
edit: for anyone curious there’s a bit of a breakdown of how it works here: https://feddit.win/comment/244427
Being a part of Lemmy in these early days has been kind of interesting, seeing all of the bugs and bits that will be ironed out over time. One day when Lemmy is as old as Reddit it will all be folklore. Maybe.
This’ll definitely be remembered. It’s good for us, we needed the wakeup call.
lemmy.blahaj.zone got hacked too, looks like the same people
They also changed the allowed/blocked instances to allow threads.net and defederate lemmy.ml, just like they did on lemmy.world: https://lemmy.blahaj.zone/instances
Huh… so this probably is more sophisticated than a single acct breach then. Lovely.
Yeah, I’d recommend any server admin that doesn’t have 2FA turn it on ASAP until we know what their exploiting
Looks like the accounts were compromised by stealing their cookie - something 2FA can’t stop.
Still should have it on, though.
blahaj admins are aware and have the site down with a splash screen now
4AM in the Netherlands where the instance owner Ruud lives… hopefully his assistant admins can clean it up, but it might be a bit before he even knows anything is wrong.
Don’t know if this will be relevant at all, but I’m almost hoping this will force Lemmy devs to abandon the obscure markdown crate they use for pulldown-cmark.
Using an obscure markdown implementation just because it supports spoiler tags always sounded like a silly decision to me!
They’re stealing jwt tokens and noting when they’re admin tokens.
https://lemmy.sdf.org/post/696053 https://lemmy.sdf.org/comment/850269
The admins now appears to have taken down the backend in an effort to stop the defacing.

Looks like this thread is getting mass downvoted by bots btw
Just went there and didn’t immediately see anything out of the ordinary, but then was redirected to Chatroulette, lol yikes
Really hoping it’s “only” redirecting to offensive sites, and not to malware. I got redirected a few times, before I closed my browser.
TBF modern browsers are remarkably secure from being a vector to pwn your computer these days.
EDIT: I don’t endorse hanging out on a compromised lemmy.world. Focus on the implication for the bigger lemmyverse though. A hack coming through to you is unlikely.
I sure hope so
~ Sent via Internet Explorer 6 on Windows XP
lol
For those not aware, the beehaw server did intentionally shut their instance down to avoid any issues.
See announcement here: https://hachyderm.io/@beehaw/110687918465426082

















